Featured
Table of Contents
- – Internet Protocol Security (Ipsec)
- – Guide To Ipsec Vpns - Nist Technical Series Pu...
- – Authentication In Ipsec Vpns
- – Understanding Ipsec Vpns
- – Ip Security (Ipsec)
- – What Is Ipsec And How Ipsec Does The Job Of ...
- – Gre Vs Ipsec: Detailed Comparison
- – What Is Ip Security (Ipsec), Tacacs And Aaa ...
- – Difference Between Ipsec And Ssl
- – Ipsec: The Complete Guide To How It Works ...
Internet Protocol Security (Ipsec)
Cryptographic keys are likewise discarded. Besides IPSec VPN, much of the best VPN suppliers can likewise utilize SSL VPN to protect your connection over the internet. Depending upon the level of security required, VPN suppliers can implement both or pick one over the other. SSL VPNs depend on the protocol.
Thus, the security and applications of IPSec VPN and SSL VPN vary. With IPSec VPN, your traffic is secure as it moves to and from private networks and hosts; in a nutshell, you can protect your whole network.
Guide To Ipsec Vpns - Nist Technical Series Publications
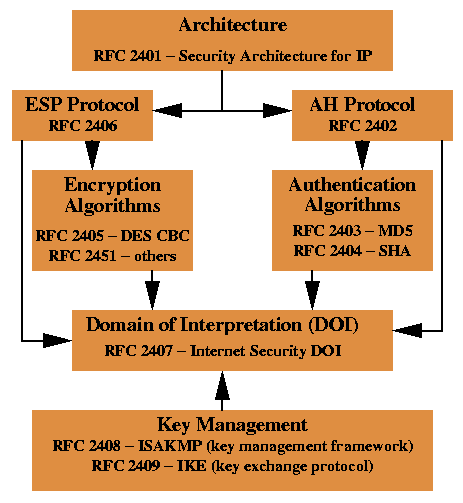
That's when you utilize IPSec. A lot of brand-new IT techs and system admins don't totally understand IPSec.
This short article will talk about what IPSec is, what it is for, how it works, and how it is various from things like SSL and TLS. IPSec is a technique of protected, encrypted interactions in between a customer and a network. That communication is sent through public networks such as the web.
Authentication In Ipsec Vpns
That means that IPSec can potentially be more safe than other techniques of protected interaction. IPSec connections are still made between the client and host through other networks.
That's since the whole package of information is secured during communications. You might think that all packets require readable headers to get to their location properly, and you would be.
Understanding Ipsec Vpns
ESP includes new header info and trailers (similar to headers however at the end of a packet) for transportation while the actual header remains encrypted. Likewise, each package is authenticated too. The IPSec host will confirm that each package of data received was sent out by the entity that the host believes sent it.
IPSec is used to develop a safe technique of interaction between a customer and a host. The host is generally a private network, too. We understand how IPsec works, but what is IPSec utilized for?
Ip Security (Ipsec)
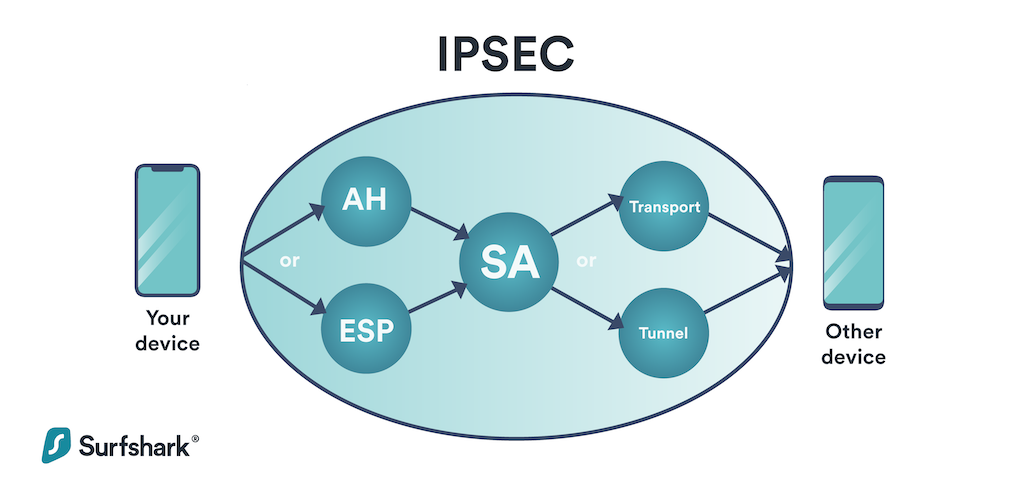
Today, however, they can interact over the open web using an IPsec connection. In numerous methods, an IPsec connection and a TLS or SSL connection are comparable. Both supply a way for protected, encrypted communications. Both can utilize public networks for communication. Etc. In numerous other ways, though, IPsec and TLS or SSL connections are extremely various, too.
Hence, IPsec connections begin at the fundamental connection level of the OSI design. In contrast, TLS and SSL connections start greater up the stack. Second, TLS and SSL connections depend on the application layer (HTTP) and layer 4 (TCP) to work. That indicates they are likewise susceptible to exploits in those layers, whereas IPsec may not be.
What Is Ipsec And How Ipsec Does The Job Of Securing ...
Due To The Fact That TLS and SSL connections utilize TCP, those safe connection types require to be worked out. As soon as negotiated, the customer and host will settle on a file encryption secret, too. IPSec is various. Communication is encrypted immediately. In fact, the secret key utilized for encryption requires to be shared in between the customer and host independently before any interactions can be attempted.
The approach used for key exchanges in IPsec is called IKEv1 or IKEv2. Due to the fact that IPsec connections are encrypted instantly, the whole header of the IP package can be secured, too.
Gre Vs Ipsec: Detailed Comparison
Network admins require to take care to make allowances for those size differences in their network. IPSec is a method of secure, encrypted interaction in between a customer and a host.
The host is typically a personal network. IPsec itself is not a procedure but rather a handful of protocols utilized together. The protocols that IPsec uses start at Layer 3 of the OSI design, making IPsec potentially more protected than things like TLS or SSL.IPsec is generally utilized for VPNs.
What Is Ip Security (Ipsec), Tacacs And Aaa ...
Virtual personal network (VPN) is an innovation for establishing a private network on a public network. It is a logical network over a public network such as the Web, enabling user data to be sent through a rational link. This is various from a standard private network, where user information is transmitted through an end-to-end physical link.
In this phase, the communicating celebrations utilize the Internet Secret Exchange (IKE) protocol to develop IKE SAs for identity authentication and crucial info exchange, and then develop IPsec SAs for safe information transmission based upon the IKE SAs. Data transmission. After IPsec SAs are developed in between the communicating celebrations, they can transfer data over an IPsec tunnel.
Difference Between Ipsec And Ssl
If the ICVs obtained at both ends are the exact same, the package is not tampered with during transmission, and the receiver decrypts the packet. If the ICVs are different, the receiver disposes of the package. IPsec file encryption and authentication process Tunnel teardown. In many cases, session aging (session disconnection) in between two communication celebrations shows that information exchange between the 2 interaction parties is total.
That is, AH makes sure that the source of IP packages is trusted and the information is not tampered with. AH, nevertheless, does not provide the file encryption function. An AH header is added to the standard IP header in each information packet. AH checks the stability of the whole IP packet.
Ipsec: The Complete Guide To How It Works ...
An ESP header is appended to the basic IP header in each data packet, and the ESP Trailer and ESP Auth data fields are added to each information package. ESP in transportation mode does not examine the integrity of IP headers. ESP can not make sure that IP headers are not tampered with.
The following compares IPsec VPN and SSL VPN: Working layers of the OSI referral model, OSI specifies a seven-layer structure for network affiliation: physical layer, data link layer, network layer, transport layer, session layer, discussion layer, and application layer. IPsec operates at the network layer and straight runs over the Web Procedure (IP).
Table of Contents
- – Internet Protocol Security (Ipsec)
- – Guide To Ipsec Vpns - Nist Technical Series Pu...
- – Authentication In Ipsec Vpns
- – Understanding Ipsec Vpns
- – Ip Security (Ipsec)
- – What Is Ipsec And How Ipsec Does The Job Of ...
- – Gre Vs Ipsec: Detailed Comparison
- – What Is Ip Security (Ipsec), Tacacs And Aaa ...
- – Difference Between Ipsec And Ssl
- – Ipsec: The Complete Guide To How It Works ...
Latest Posts
10 Best Vpn Services For 2023 - Top Vpns Compared
15 Leading Vpn Software For Startups For 2023
Best Vpn Services - 9 Top Picks For July 2023
More
Latest Posts
10 Best Vpn Services For 2023 - Top Vpns Compared
15 Leading Vpn Software For Startups For 2023
Best Vpn Services - 9 Top Picks For July 2023